"We don't" is the short answer. It's unfortunate, but true.
How do you know there isn't a logic bug that spills server secrets through an uninitialized buffer? How do you know there isn't an enterprise login token signing key that accidentally works for any account in-or-out of that enterprise (hard mode: logging costs more than your org makes all year)? How do you know that your processor doesn't leak information across security contexts? How do you know that your NAS appliance doesn't have a master login?
This was a really, really close one that was averted by two things. A total fucking nerd looked way too hard into a trivial performance problem, and saw something a bit hinky. And, just as importantly, the systemd devs had no idea that anything was going on, but somebody got an itchy feeling about the size of systemd's dependencies and decided to clean it up. This completely blew up the attacker's timetable. Jia Tan had to ship too fast, with code that wasn't quite bulletproof (5.6.0 is what was detected, 5.6.1 would have gotten away with it).
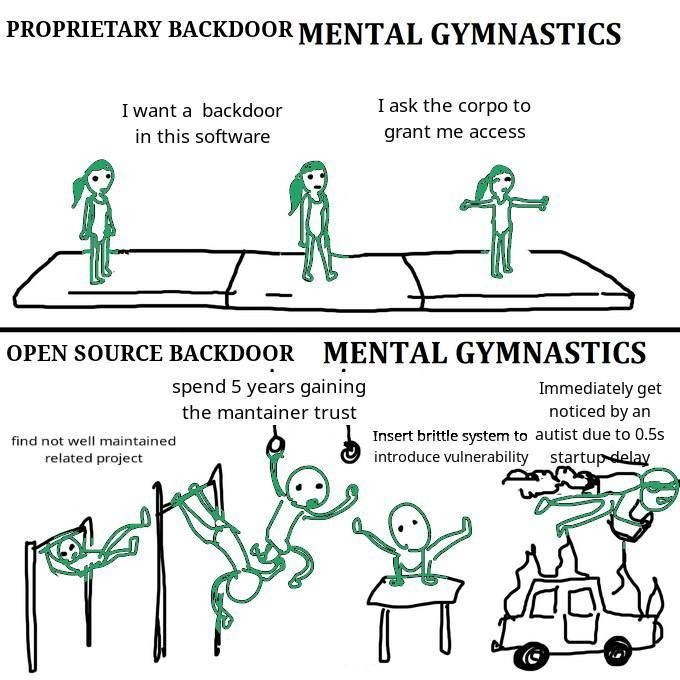
In the coming weeks, you will know if this attacker recycled any techniques in other attacks. People have furiously ripped this attack apart, and are on the hunt for anything else like it out there. If Jia has other naughty projects out here and didn't make them 100% from scratch, everything is going to get burned.
Self hosting personal photos doesn't generally require opening anything up to the internet, so most backdoors would not be accessible by anyone but you.
You don't. Hackers often exploit things like this for ages before they are found. Every bit of non simple software also has bugs.
But chances are you won't be the target.
Just keep everything updated and you should be alright.
Cheeky answer:

Actual answer:
Theoretically anyway, open source software's guarantee of "no backdoor" is that the code is auditable, and you could study it and know if it has any holes and where. Of course, that presumes that you have the knowledge AND time to actually go and study thousands of lines of code. Unrealistic.
Slightly less guaranteed but still good enough to calm my mind, is the idea that there is a whole-ass community of people who do know their shit and who are constantly checking this.
Do note that like. Closed source software is known to be backdoored, only, the backdoors are mostly meant for either the owners of the software (check the fine print folks) or worse, the governments.
The biggest thing that you should note is that: It is unlikely that you (or I or most of the people here) are interesting enough that anyone will actually exploit those vulnerabilities to personally fuck you over. Your photos aren't interesting enough except as part of a mass database (which is why Google/Facebook want them). Same for your personal work data and shit.
Unless those backdoors could be used to turn your machine into a zombie for some money-making scheme (crypto or whatever) OR you're connected to people in power OR you personally piss off someone who is a hacker -- it is very unlikely you'll get screwed over due to those vulnerabilities :P
Just a point to add: this backdoor was (likely) planned years in advance; it took ONE guy a couple weeks (after the malicious code was released) to find it because he had nothing else going on that evening.
I'm relatively confident that the FOSS community has enough of that type of person that if there are more incidents like this one, there's a decent chance it'll be found quickly, especially now that this has happened and gotten so much attention.
That's the neat part, we don't!
...but, we at least can have a shot of finding them.
In the meantime, I'd advise you to keep an eye out and maybe look into threat models. As people said in this thread already, bad actors probably don't care about your personal photos.
Unless OP is a celebrity or politician. Or knows they have an enemy with the resources to find and exploit potential backdoors.
I would say you can't, but if you are using open source software, then somebody can and will find them eventually and they will be patched. Unlike with closed source software, you will never know if it has a backdoor or not. This whole episode shows both the problems with open source, being lack of funding for security audits, and the beauty of open source, being that eventually it will be detected and removed.
We don’t.
I'm pretty sure most closed source software is already backdoored.
It's a feature!
Afaik, most phones are backdoored that can be abused using tools like "pegasus" which led to a huge indignation in Hungary. I don't belive PCs are exceptions. Intel ME is a proprietary software inside the CPU, often considered as a backdoor in Intel. AMD isn't an exception. It's even weirder that Intel produces chips with ME disabled for governments only.
We can't know. If we would know, those weren't undetected backdoors at all. It's not possible to know something you don't know. So the question in itself is a paradox. :D The question is not if there are backdoors, but if the most critical software is infected? At least what I ask myself.
Do you backups man, do not install too many stuff, do not trust everyone, use multiple mail accounts and passwords and 2 factor authentication. We can only try to minimize the effects of when something horrible happens. Maybe support the projects you like, so that more people can help and have more eyes on it. Governments and corporations with money could do that as well, if they care.
The main solace you can take is how quickly xz was caught: there is a lot of diverse scrutiny on it.
Hmm, not really. It's only because it nerd-sniped someone who was trying to do something completely unrelated that this came to light. If that person has been less dedicated or less skilled we'd still probably be in the dark.
Call me names... But sometimes the story has far more branched backstories than they actually shed into light.
Trust nobody, not even yourself.
Check the source or pay someone to do it.
If you're using closed source software, its best to assume it has backdoors and there's no way to check.
Even if there are nation state level backdoors, your personal server is not a valuable enough target to risk exposing them. Just use common sense, unattended-upgrades, and don't worry too much about it.
We don't. That's why we use multiple layers of security. For example keeping all services accessible only via VPN and using a major OS that a lot of production workloads depend on such as Debian, Ubuntu LTS or any of the RHEL copycats. This is a huge plus of the free tier of Ubuntu Pro BTW. It's commercial level security support for $0. Using any of these OSes means that the time between a vulnerability being discovered, patched and deployed is as short as possible. Of course you have to have automatic security updates turned on, unattended-upgrades in Debian-speak.
I do IT security for a living. It is quite complicated but not unrealistic for you to DIY.
Do a risk assessment first off - how important is your data to you and a hostile someone else? Outputs from the risk assessment might be fixing up backups first. Think about which data might be attractive to someone else and what you do not want to lose. Your photos are probably irreplaceable and your password spreadsheet should probably be a Keepass database. This is personal stuff, work out what is important.
After you've thought about what is important, then you start to look at technologies.
Decide how you need to access your data, when off site. I'll give you a clue: VPN always until you feel proficient to expose your services directly on the internet. IPSEC or OpenVPN or whatevs.
After sorting all that out, why not look into monitoring?
Fun fact, you can use let's encrypt certs on a internal environment. All you need is a domain.
Just be aware that its an information leakage (all your internal DNS names will be public)
you don't and will never will. I would recommend reading a lecture by Ken Thompson the co-creator of Unix for more details on this https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
We dont.
This was likely a state-sponsored attack. If your SSH isn't exposed to the internet this probably wouldn't have effected you. Also most people run stable distros like Debian on their server, and this particular vulnerability never made it to the stable branch. I would guess that most of the computers you have ever used have backdoors. Even if you run Linux (which may itself have some) you might still have a proprietary UEFI on your motherboard. Something like xz wouldn't effect you because no government really cares what's on your server. Smaller attacks can be avoided through common sense. Some people will expose services that require zero authentication to the internet. Follow basic best practices and you will probably be fine.
Edit: Also remember, google photos once flagged a picture of a child that the child's father had taken for medical reasons as abuse, so self-hosted may not be completely private or secure, but it's better than the alternative.
We don’t know. However, no one cares about your personal photos ; no one will ever attempt to hack you specifically unless you’re a high value target (in which case, stop hosting your photos anywhere immediately)
The only thing that could get your photos is if an undiscovered backdoor is exploited by someone doing some sort of a mass attack. As far as I know, they’re pretty rare, because people with the means to do them generally have a specific set of people they care about (which you are unlikely to be a part of).
We don’t know. However, no one cares about your personal photos ; no one will ever attempt to hack you specifically unless you’re a high value target (in which case, stop hosting your photos anywhere immediately)
To those assumptions I would say : we don't know. Personal vendettas do exist and we cannot look into the minds of individuals going crazy neither.
no one will ever attempt to hack you
My brother in Christ, how do you think botnets get built?
We don't know. But if there were well known backdoors to mainstream security practices we might see more companies that depend on security shutting down, or at least shutting down their online activities. Banks, stock trading, crypto exchanges, other enterprises that handle money, where hacking would be lucrative.
I don't think you need to worry about backdoors with most of those. Worry more about unfixed security holes due to an extreme emphasis on "stability" as in using old versions when fixes have already been released when it comes to anything hosted by large companies.
Good question. I have asking myself the same thing as well. In case of ssh it is possible to use 2FA with a security key, which is something I'd like to put in my todo.txt
If backdoors exist, they’re probably enough to get your data no matter where it’s stored, so self hosting should be fine. Just keep it up to date and set up regular automatic backups.
Reading the source code for everything running on your machine and then never updating is the only way to be absolutely 100% sure.
Even with that you will miss something
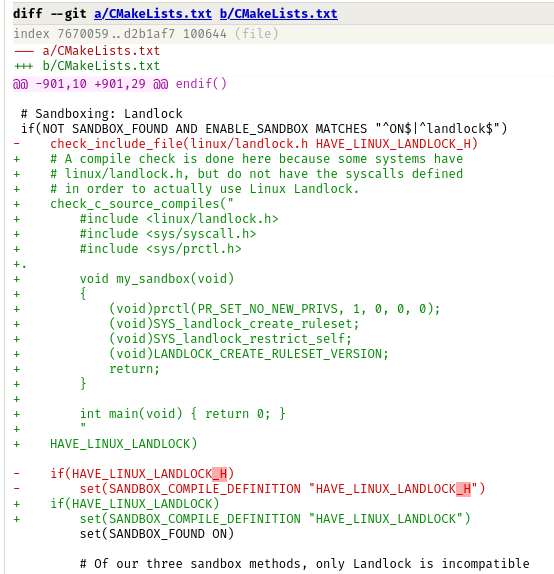
This is a sliver of one patch, there is a bug here that disabled a build tool that breaks the attack. Can you find it?
The best you can do is use OSS software that has been battle tested. Stuff like OpenSSH and OpenVPN are very unlikely to have backdoors or major vulnerabilities currently being exploited. If you don't trust something to not be vulnerable, you're best to put it behind a more robust layer of authentication and access it only by those means.
I'm not a security specialist either. I learn new things every day, but this is why my NextCloud is accessible through TailScale only and I have zero ports exposed to the outside world.
The only real convenience I lose is being able to say "check out this thing on my personal server" with a link to someone outside my network, but that's easily worked around.
if you are self hosting and enjoy over-engineering systems... VLANS, ACLs between subnets and IDS/IPS should be part of.your thinking. separate things into zones of vulnerability / least-privilege and maintain that separation with an iron fist. this is a great rabbit hole to fall down if you have the time. however, given a skilled adversary with enough time and money, any network can be infiltrated eventually. the idea is to try to minimize the exposure when it happens.
if the above is not a part of your daily thinking, then don't worry about it too much. use a production OS like Debian stable, don't expose ports to the public internet and only allow systems that should initiate communication to the internet to actually do so (preferably only on their well known protocol ports - if possible).
You never know what security holes exist until they're exploited. Nothing you can really do about that. Security and convenience have always, and will always, be a trade off and a matter of personal acceptability. If you host anything, it will be potentially vulnerable, way less so if you take proper precautions. If you're not just overtly insecure, you'll probably be fine, but there's no way to say for sure.
That's the neat part, you don't. However if you stay up to date it is not a big deal.
Well not too up to date as we just have witnessed 😁
Just use a stable system
While others are saying “no one cares about your personal photos” personal info is not the target of backdoor attacks like this. It’s more likely an attempt to get access to lots of processing power for a crypto mine or botnet.
It’s best practice to have the minimum packages required to run whatever service you are running, don’t add other stuff that you won’t be using. Using a distro that is “outdated” like Debian stable can help since the packages have had more time out in the wild to be tested.
I am sure that the xz incident has raised a lot of alarms across many projects.
Linux
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Rules
- Posts must be relevant to operating systems running the Linux kernel. GNU/Linux or otherwise.
- No misinformation
- No NSFW content
- No hate speech, bigotry, etc
Related Communities
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0