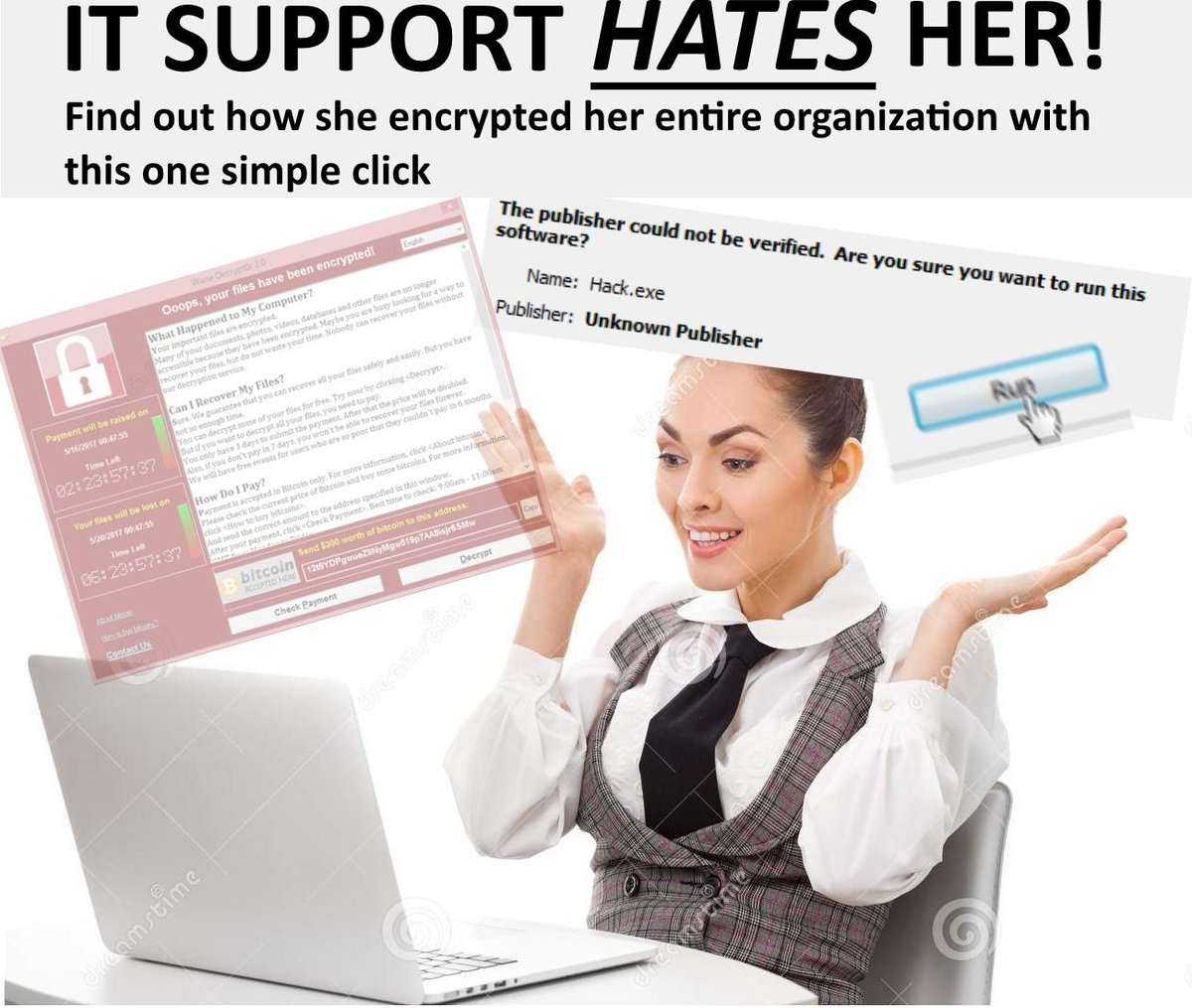
if an end user can serve as an entry point to the entire domain for ransomware, the end user hasn't failed, IT has.
196
Be sure to follow the rule before you head out.
Rule: You must post before you leave.
Upper management: "GIVE ADMIN PRIVELEGES TO ALL ACCOUNTS TO STREAMLINE THINGS. I DON'T CARE IF ITS INSECURE DO IT!"

[Fired for noncompliance]
Sad truth of IT. Being ordered around by tech illiterate bosses who refuse to listen. And they often don't even seem to value their employees, thinking they're easily replaced (they aren't)
But sire, our employees will be in potential violation of SOC 2 compliance should we be audit—- “JUST DO IT!”
Today I got an email from management, something along the lines of "you didnt click the link in this email we sent as a required questionnaire about phishing, some people reported it as phishing: a reminder, all emails from IT@company.com are not phishing"
There was no previous email
I checked the message details and it said "THIS IS A PHISHING TEST BY external company"
It was a phishing test disguised as an urgent reminder to answer a phishing questionnaire, replying to a nonexistent email. I can't wait until Monday when they round up everyone who clicked the link
This is a good one. We get standard phishing tests which make no sense. It is usually a person I don't know, from a company I haven't heard of asking me to edit/review a file they share. People who design these tests should know that people do NOT jump into the opportunity of editing/reviewing files or receiving tasks. I imagine real phishing attacks must be smarter than this.
Not nessecarily. They only need one person to run the file
I work for a small-ish but fast-growing municipality, and we're getting increasingly well-targeted actual attacks. Instead of posing as "The IT department" they're posing as my boss or the City Manager by name.
This week they even started name-dropping the conference most of the directors were actually attending as an excuse why we wouldn't be able to reach out and talk to them before the "request$ was due.
Wow damn that'd trick whole swaths of our org 🤦. Sad how many people we still get with the super obvious "Free $5 on Venmo" phishing tests...
That's actually pretty smart.
They did something similar at our university, I wonder how many fell for it. They never told us
Usually a company needs a ransomware attack or some other digital tragedy before they learn the importance of security.
Sometimes they need a few incidents, and need to be reminded when upper management deprioritizes IT security.
Nothing like running a ransomware on a government computer causing huge leak on a government run health database exposing everyone to a potential security risk.
And this is why I decided to not do IT.
She probably doesn't do IT and that's the problem.
I don't mind, that not the support departments job, probably more like Info sec or dev ops or something.
laughs in small company
Mr.Robot.jpg