this post was submitted on 23 Aug 2023
76 points (95.2% liked)
Linux
48083 readers
785 users here now
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Rules
- Posts must be relevant to operating systems running the Linux kernel. GNU/Linux or otherwise.
- No misinformation
- No NSFW content
- No hate speech, bigotry, etc
Related Communities
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0
founded 5 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
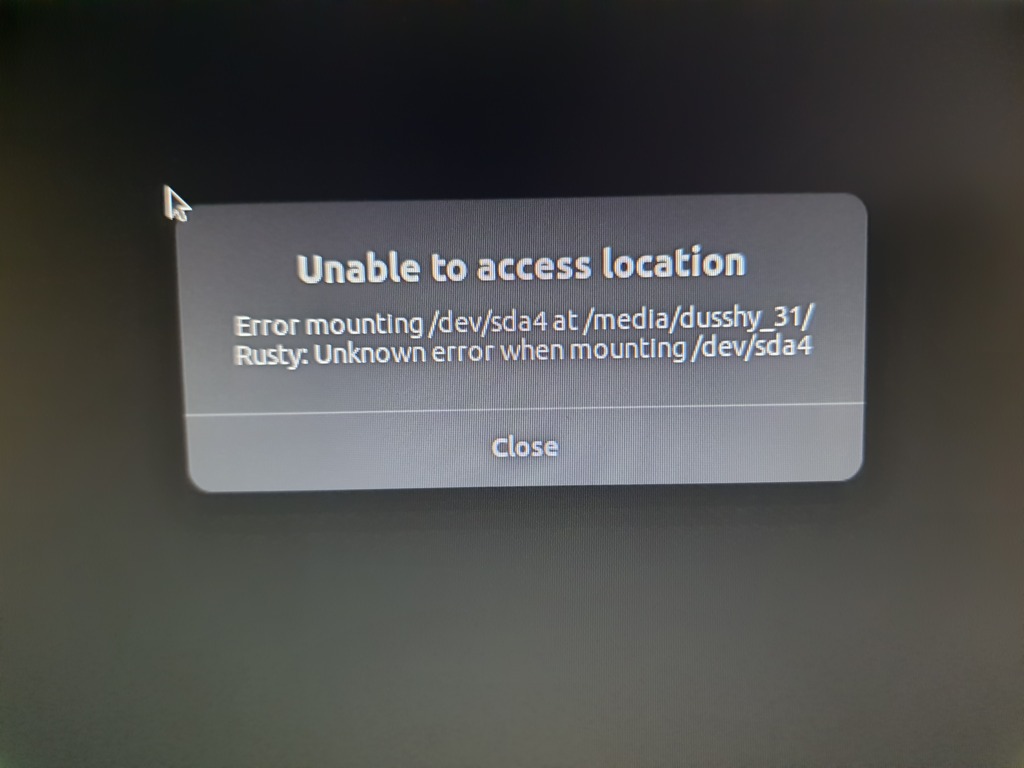
sda-debug.shchmod +x sda-debug.shsudo ./sda-debug.sh/tmp/sda-debug.loghereEDIT: changed the script to log everything to a file for easier copy-past-ability.
This script will unmount the problematic drive and try to mount it to another place
/tmp/myprecious, a temporary place. Then, as it says, will attempt to read and then write to the drive. Finally, it removes the file it wrote to test writeability, unmounts the drive again and removes the temporary mount place. The scripts needs root access to mount and unmount and possibly to write and read.Please don't run a script you found on the internet with root access without knowing what it does.
This is some very good advice, OP!
Make this a gist and post a link. Will solve all formatting errors.
I would remove the formatting of the script. For me that would never run as a bash script as it's filled with markup. Not sure if it shows up nicely for you or not so figured I'd let.you know it may not be displaying for others at least.
If you follow the link to the original post, it displays correctly. For some reason, Lemmy sends HTML for code blocks. kbin rightly escapes it on their end for security.
https://codeberg.org/Kbin/kbin-core/issues/649
https://codeberg.org/Kbin/kbin-core/issues/724
https://github.com/LemmyNet/lemmy/issues/3648
Thanks for the info. Makes sense.
Ampersand was escaped in web UI, editted to reflect that. Everything else is displayed fine.
Considering the first line is a span block, I don't think you realize what you see is not necessarily what others see.
I now understand the issue better, but since it's a request from a lemmy user and the issue appears to be on kbin - I'll leave it as is.
Makes sense. Though I'll note I find folks find help via methods of others asking for the same thing so a Kbin user could easily come across this post trying to find an answer to a similar problem. That being said, I don't have a good suggestion for a workaround so leads me back to "makes sense."
Only kbin users are seeing what you see. It looks fine on other Lemmy instances.
Lemmy and kbin do weird things with code blocks. From the source, the post itself clearly only contained backticks. Lemmy sends out marked-up text. kbin escapes it.
curl -i -X GET -H 'Accept: application/activity+json' https://lemmy.cafe/comment/1368187https://pastebin.com/VT4gmJTJ
Code link for anyone that wants it.