this post was submitted on 09 May 2024
749 points (99.2% liked)
Funny
6826 readers
548 users here now
General rules:
- Be kind.
- All posts must make an attempt to be funny.
- Obey the general sh.itjust.works instance rules.
- No politics or political figures. There are plenty of other politics communities to choose from.
- Don't post anything grotesque or potentially illegal. Examples include pornography, gore, animal cruelty, inappropriate jokes involving kids, etc.
Exceptions may be made at the discretion of the mods.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
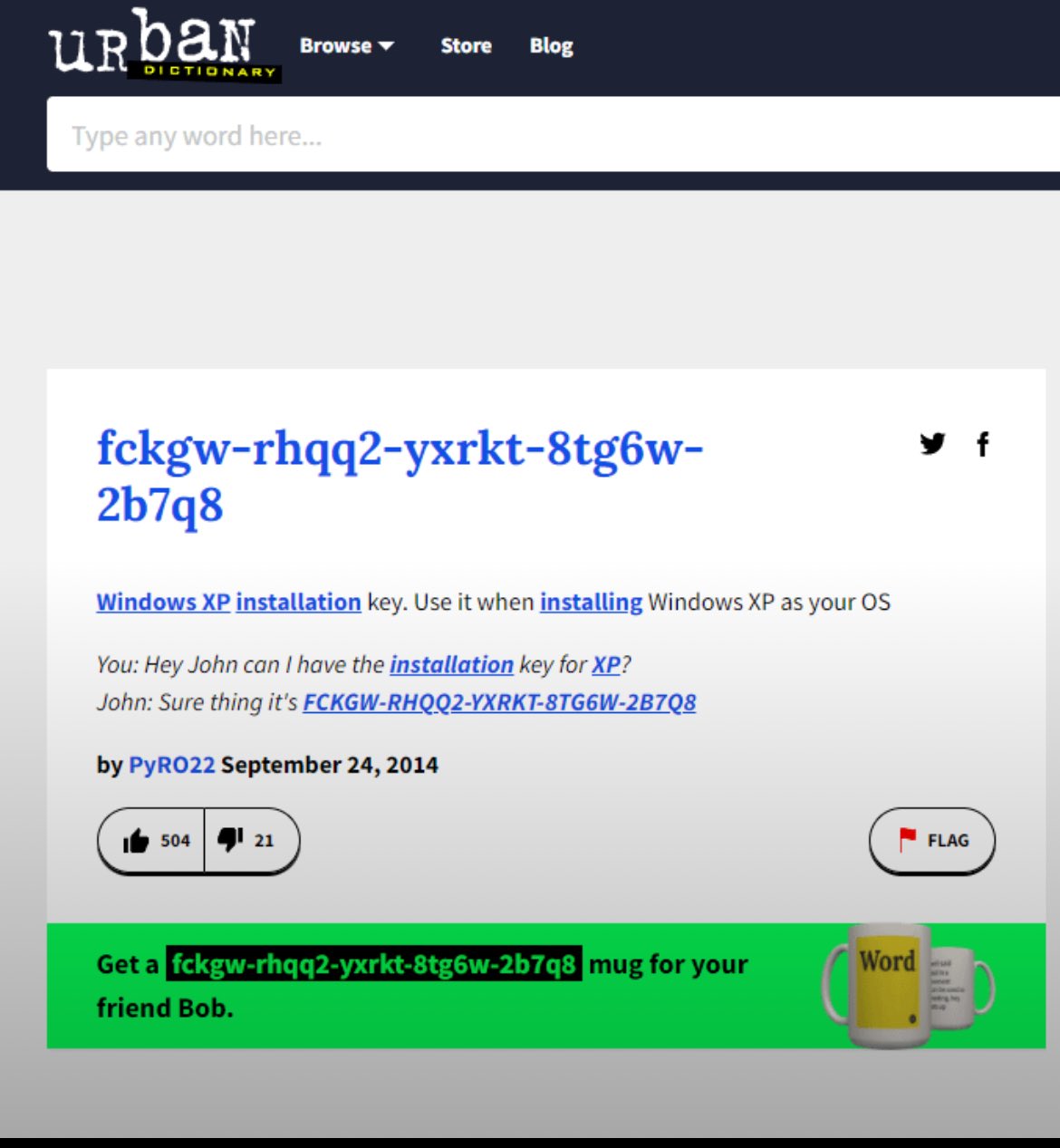
I don't know if it still works, but I found a "cheat" for free windows back in the day that I even upgraded into 10 with lol
My friend had an "upgrade" code for XP that he gave me, so when I installed windows and tried to use the code it gave me the whole "this is an upgrade code not a new code" kind of message. I rebooted the PC and used the same installer to "upgrade" my newly installed windows XP to windows XP. Same install, just did it again basically. It then accepted the code as valid lol
Today's kids use the activation scripts on GitHub which is owned by Microsoft. Just open cmd and run
irm https://massgrave.dev/get | iexIt will download the code storef here: https://github.com/massgravel/Microsoft-Activation-Scripts and run it, then windows is activated.
you can also use it to upgrade from home to pro/enterprise for free
I used it for the office suite. I should really look at using it for an OS upgrade one day
what part of it is untrusted?
all components of it are open source, down to the proxy dlls and activation scripts
yeah
irm ... | iexis basically the direct windows equivalent of pipe to bash but eh.... you can download the script from github, unpack it and run manually if you wantFor a while you could just remove all the permissions from the activation nagware on a trial install and it would run fine, and you'd even get updates. At some point they added some service which would periodically check those permissions and revert them, and I was never able to figure out what that process was.
Which means that there is apparently now a hidden user and access tier which exists solely to monitor windows system permissions, and I feel like this is my most noteworthy legacy in a small way.
Much like the abrahamic god, I love loopholes.