this post was submitted on 26 Mar 2024
1284 points (98.4% liked)
Curated Tumblr
3942 readers
115 users here now
For preserving the least toxic and most culturally relevant Tumblr heritage posts.
Image descriptions and plain text captions of written content are expected of all screenshots. Here are some image text extractors (I looked these up quick and will gladly take FOSS recommendations):
-web
-iOS
Please begin copied raw text posts (lacking a screenshot that makes it apparent it is from Tumblr) with:
# This has been reposted here to Lemmy as part of the "Curated Tumblr Project."
I made the icon using multiple creative commons svg resources, the banner is this.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
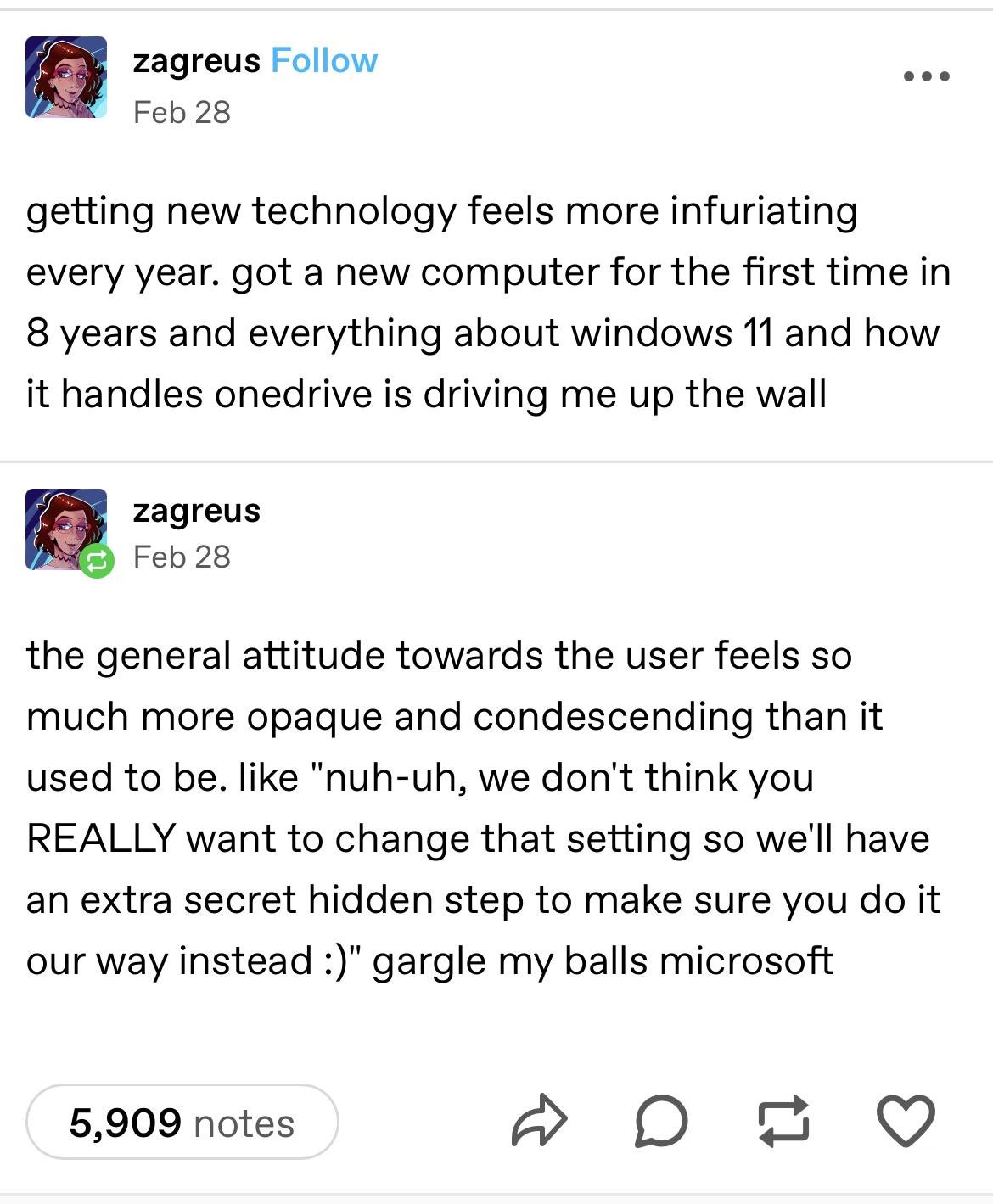
I've done support for sysadmins and I've run into a lot of them who don't understand the concept of relative or absolute paths. A couple weeks ago I had to explain how password hashing works to people working for a huge aerospace company.
I think most people learn to use computers like they learn to use a car, in that they understand the rituals they need to perform to get it to do the thing they want. They lack understanding of what's going on under the hood so when something goes wrong they can't fall back on knowledge and figure out what went wrong, they have to learn an entirely new routine to fix it instead of learning the principles and thinking critically.
Adeptus Mechanicus Intensifies
I've been catching myself calling it the activation rune instead of the power button.
I've worked as a sysadmin for 4 years and was recently offered a position as IT security consultant, and I don't know how password hashing works. (Don't worry, I rejected the position)
Thank you for not becoming yet another turtle on a post.
Plus it wasn't even how the hashing works, just explaining how a system can check if a password is correct without decrypting the password. They're getting millions of my tax dollars to build this IT system for the military and they don't even understand that one-way hashes exist.