this post was submitted on 05 Jan 2024
297 points (100.0% liked)
196
16503 readers
2268 users here now
Be sure to follow the rule before you head out.
Rule: You must post before you leave.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
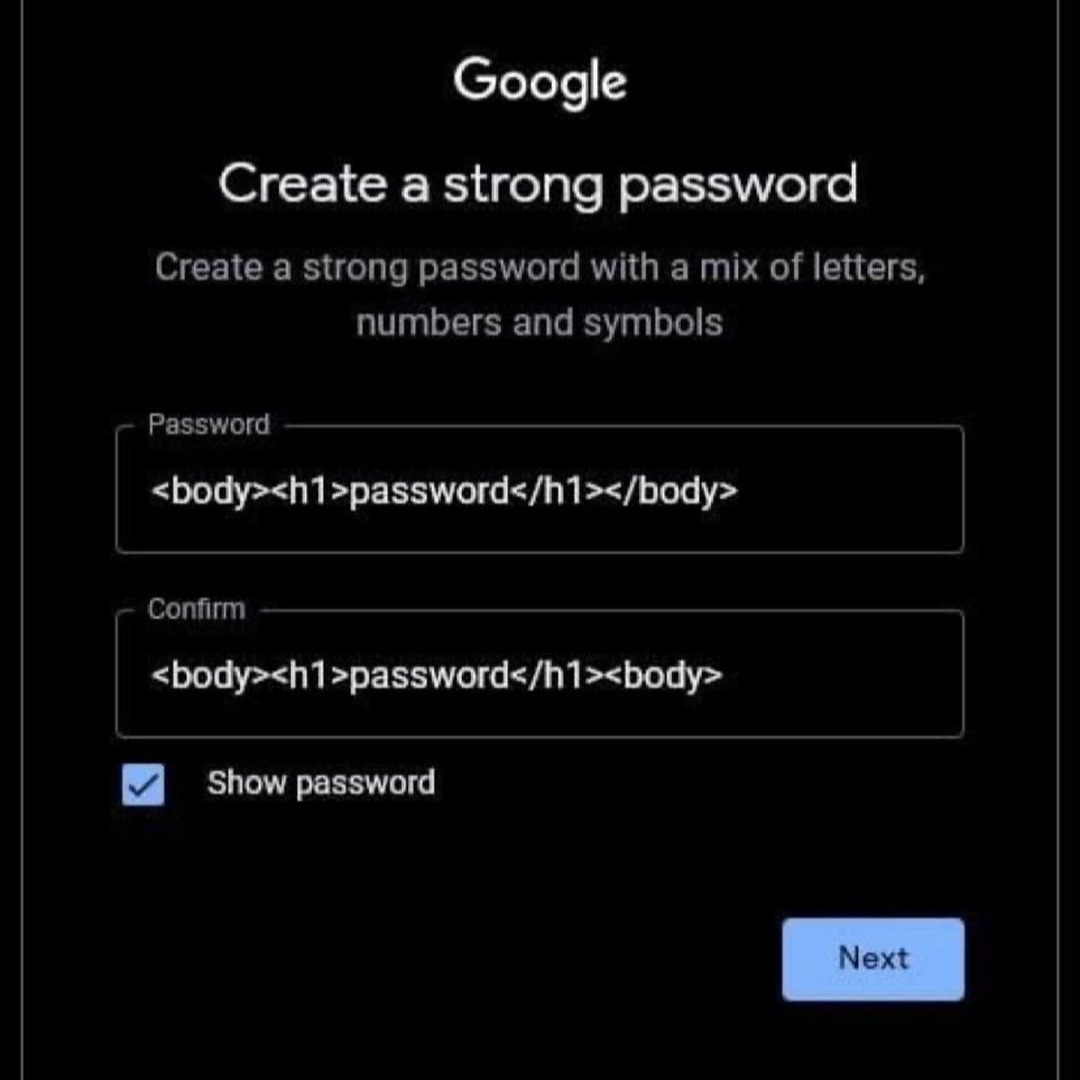
explanation for the tech illiterate (me)?
I'm not an expert but I think this is code that can be used to make text larger and bolder- in other words, STRONG text.
And you can see that the text being modified by those commands, in the middle of them... is 'Password'
So they're literally creating a Strong Password
You can take this a step further to segregate passwords as well.
Reusing passwords across devices is bad. If one gets compromised you don’t want a password being out into a brute force table to be used with all your other accounts elsewhere.
This method of tagging using HTML markup styles in your passwords lets you keep the same core passphrase but alter the tagging, specific to the service.
You can do this easily while also giving you artificial password complexity.
Example:
Core passpgrase is “yogurt”
Password for gmail becomes markup with a yogurt
I only need to remember yogurt.
Every device just gets a truncated service tag appended to the beginning and end using HTML style tags.
Suddenly you have a 26+ character password that you don’t forget and doesn’t compromise you across other services because each is different.
Sure they are different, but if somehow someone finds out just one password of yours, all others are broken too, right?
Right, there shouldn't be an easy to decipher password rule. Random passphrases seem to make the strongest passwords these days, especially if symbols, numbers, and spaces are allowed and used. Even the strongest password should have 2FA, and even that is only as strong as the identity verification of the password/2FA reset process.
Even rigid, known password rules are fine as long as there are enough possible combinations. xkcd.com/936/
You don’t partially decrypt passwords. You either get the full thing or you get gobble.
So if they get 1, they still don’t know you use or or etc. I wouldn’t just straight up say “Netflix” in my service tagging.
Depends on the implementation of different login services and the number of possible permutations. An attacker will probably get locked out of trying to log in after making dozens of guesses.