this post was submitted on 20 Sep 2024
450 points (98.3% liked)
Programmer Humor
19623 readers
28 users here now
Welcome to Programmer Humor!
This is a place where you can post jokes, memes, humor, etc. related to programming!
For sharing awful code theres also Programming Horror.
Rules
- Keep content in english
- No advertisements
- Posts must be related to programming or programmer topics
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
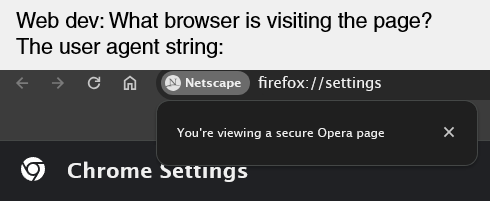
Aren't user agents just a plain text header? Couldn't a malicious agent just spoof a legitimate one?
That's correct, it is just plain text and it can easily be spoofed. You should never perform an auth check of any kind with the user agent.
In the above examples, it wouldn't really matter if someone spoofed the header as there generally isn't a benefit to the malicious agent.
Where some sites get into trouble though is if they have an implicit auth check using user agents. An example could be a paywalled recipe site. They want the recipe to be indexed by Google. If I spoof my user agent to be Googlebot, I'll get to view the recipe content they want indexed, bypassing the paywall.
But, an example of a more reasonable use for checking user agent strings for bots might be regional redirects. If a new user comes to my site, maybe I want to redirect to a localized version at a different URL based on their country. However, I probably don't want to do that if the agent is a bot, since the bot might be indexing a given URL from anywhere. If someone spoofed their user agent and they aren't redirected, no big deal.